Wireguard Site to Site VPN using Debian 11 & EdgeRouter X
By Ward Pieters on
Intro
This blog post will describe the struggle I went through to set up a Site to Site VPN using two Debian VMs and an EdgeRouter X on both sides of the connection, so you (and future me) don't have to. The image below describes my network setup. The public IP addresses are not displayed for obvious reasons.
Port forward
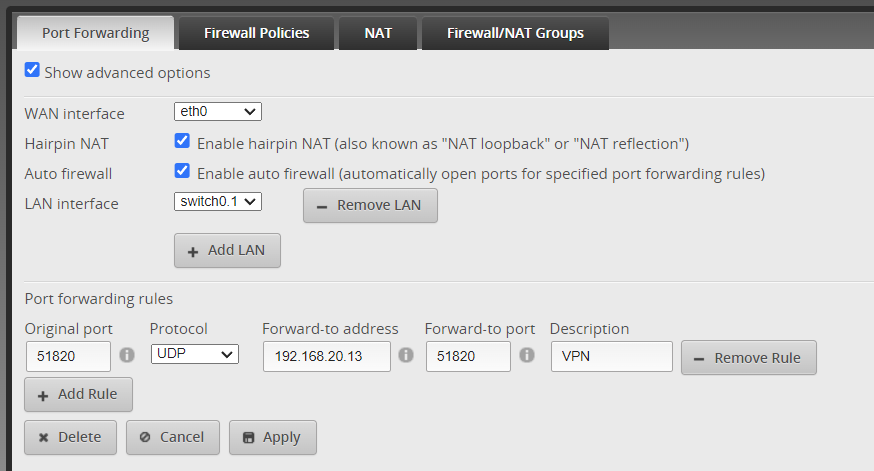
The WireGuard server (host A) must be reachable from the internet. Therefore you’ll have to port forward UDP port 51825 on Host A (server). The screenshot below shows how to set this up on a EdgeRouter X. Port forwarding is not necessary on host B as this VM acts as a client.
VM Setup
Note: to do this yourself, some knowledge of networking and Linux is required.
To start, I installed Debian 11 running WireGuard on two VMs. The process is basically the same on Ubuntu.
apt-get update
apt-get install -y wireguard iptables
Before we go any further, we need to edit the /etc/sysctl.conf file on both hosts. Add the line shown below to the file and run sysctl -p.
net.ipv4.ip_forward=1
WireGuard Setup
After setting up the VMs, WireGuard is installed and some commands are now available for us to use. We will use them to generate the public and private key for the config files. First we will do this on Host A (server):
wg genkey > host-a.key
wg pubkey < host-a.key > host-a.pub
And then on host B (client):
wg genkey > host-b.key
wg pubkey < host-b.key > host-b.pub
We will use the contents of the generated files in the WireGuard configuration. On host A (server) we create the file /etc/wireguard/wg0.conf with the content below. Replace the placeholders (e.g. <host-a.key>) with the content of the appropriate files and make sure to replace eth0 with your actual network interface.
[Interface]
PrivateKey = <host-a.key>
Address = 10.229.76.1/24
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
MTU = 1420
ListenPort = 51820
SaveConfig = false
### begin host-b
[Peer]
PublicKey = <host-b.pub>
AllowedIPs = 10.229.76.2/32, 192.168.10.0/24
PersistentKeepalive = 16
### end host-b
Then we'll create the file /etc/wireguard/wg0.conf on host B (client), but with different content. Make sure to replace eth0 with your actual network interface and the Endpoint with the IP address of host A (server).
[Interface]
PrivateKey = <host-b.key>
Address = 10.229.76.2/24
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = <host-a.pub>
Endpoint = 213.x.x.x:51820
AllowedIPs = 192.168.20.0/24
PersistentKeepalive = 16
On both hosts we set the WireGuard interface to start on boot and right now by running systemctl enable wg-quick@wg0 --now. If you did everything okay, you should not see any errors.
Routing
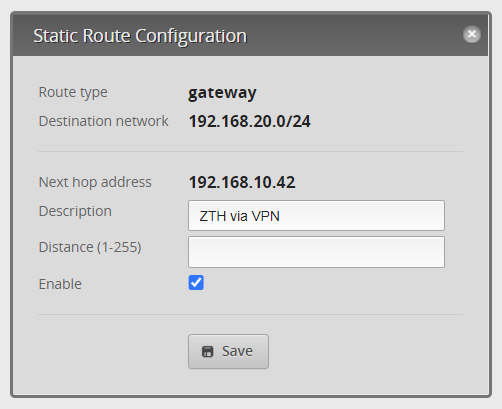
On the EdgeRouter of both networks you add a static route by clicking on 'Add Static Route' and then entering the information below. On the router of host A add the IP range of host B as destination network and the IP of host A as next hop address. The same goes for the router in the network of host B, but then the other way around.
Note: adjust the IP ranges to your situation!